Zero Trust Security: Implementing Robust IAM for Cloud Environments
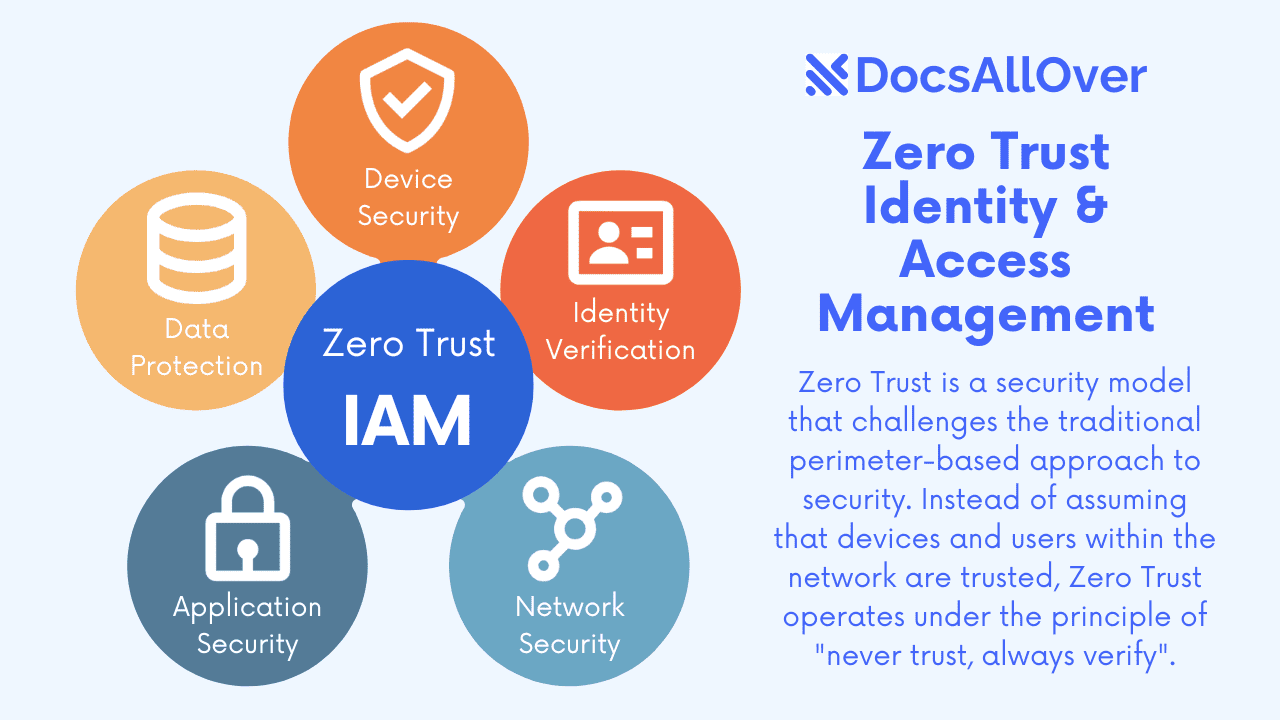
What is Zero Trust?
Zero Trust is a security model that challenges the traditional perimeter-based approach to security. Instead of assuming that devices and users within the network are trusted, Zero Trust operates under the principle of "never trust, always verify."
Key principles of Zero Trust include:
- Least Privilege: Granting users and devices only the minimum necessary access to resources.
- Continuous Authentication and Authorization: Continuously verify the identity and authorization of users and devices, regardless of their location.
- Micro-segmentation: Isolate and segment networks and applications to limit the impact of potential breaches.
- Data-centric security: Focus on protecting data itself, regardless of where it resides.
The Importance of Zero Trust in the Cloud
The rise of cloud computing has significantly increased the attack surface for organizations.
- Increased Reliance on Cloud Services: Many organizations rely heavily on cloud services for various functions, such as data storage, application hosting, and business operations. This reliance on cloud services makes them more vulnerable to cyber threats.
- Growing Threat Landscape: The threat landscape is constantly evolving, with new and sophisticated threats emerging regularly. Ransomware attacks, data breaches, and other cyberattacks are becoming increasingly common and costly.
- Need for Enhanced Security Posture: In this dynamic environment, a traditional perimeter-based security model is no longer sufficient. Zero Trust provides a more robust and adaptive approach to security in the cloud.
By implementing a Zero Trust security model, organizations can significantly enhance their security posture, reduce the risk of data breaches, and improve their overall resilience to cyber threats.
Key Components of Zero Trust IAM
Zero Trust security relies heavily on robust Identity and Access Management (IAM) solutions. Here are some key components:
- Strong Authentication and Authorization:
- Multi-Factor Authentication (MFA): Requires users to provide multiple forms of verification (e.g., password, biometrics, one-time codes) to access resources, significantly enhancing security.
- Single Sign-On (SSO): Allows users to access multiple applications and resources with a single set of credentials, improving user experience and reducing the risk of credential theft.
- Least Privilege Access Control (Principle of Least Privilege): Grant users and devices only the minimum necessary access to perform their job duties, reducing the potential impact of a successful compromise.
- Role-Based Access Control (RBAC): Assigns permissions based on user roles and responsibilities within the organization.
- Attribute-Based Access Control (ABAC): Goes beyond RBAC by considering various attributes (e.g., location, device type, time of day) to make access control decisions.
- Data Encryption and Protection:
- Data Encryption at Rest: Encrypt data stored on servers, databases, and other storage devices to protect it from unauthorized access.
- Data Encryption in Transit: Encrypt data during transmission to protect it from eavesdropping and interception.
- Data Loss Prevention (DLP) Solutions: Implement DLP solutions to identify, monitor, and prevent the unauthorized movement of sensitive data.
- Device and Network Security:
- Endpoint Security: Implement robust endpoint security measures, including antivirus, anti-malware, and intrusion detection/prevention systems (IDPS) on all devices accessing the network.
- Network Segmentation and Micro-segmentation: Isolate critical systems and data by segmenting the network into smaller, more secure zones. Micro-segmentation further isolates individual workloads and applications within the network.
- Secure Remote Access Solutions: Implement secure remote access solutions such as Virtual Private Networks (VPNs) or Virtual Desktop Infrastructure (VDI) to protect sensitive data and prevent unauthorized access from remote locations.
By implementing these key components, organizations can establish a strong foundation for Zero Trust security within their cloud environments.
In the next section, we will discuss how to implement Zero Trust principles in cloud environments.
Implementing Zero Trust in Cloud Environments
- Cloud Provider IAM Solutions:
- Leveraging Cloud Provider's Native IAM Services: Cloud providers like AWS (IAM), Azure AD, and GCP IAM offer robust built-in identity and access management services. These services provide granular control over user access, resource permissions, and security policies.
- Implementing Security Groups and Network Access Control Lists (ACLs): Utilize security groups and network ACLs to control traffic flow within the cloud environment. This allows you to create fine-grained network segmentation and restrict access to resources based on IP addresses, ports, and protocols.
- Third-Party IAM Solutions:
- Integrating with Third-Party IAM Providers: Organizations can integrate with third-party IAM providers (e.g., Okta, Auth0) to enhance their security posture. These solutions often provide advanced features like single sign-on (SSO), multi-factor authentication (MFA), and identity federation.
- Evaluating and Selecting the Right IAM Solution:
- Carefully evaluate the specific needs and requirements of your organization.
- Consider factors such as cost, features, scalability, integration capabilities, and vendor support.
- Choose an IAM solution that aligns with your overall security strategy and business objectives.
By effectively leveraging cloud provider IAM services and integrating with third-party solutions, organizations can implement robust access controls and enhance their overall security posture in the cloud.
In the next section, we will discuss the importance of continuous monitoring and improvement in a Zero Trust framework.
Continuous Monitoring and Improvement
Continuous monitoring and improvement are crucial for maintaining a strong Zero Trust security posture.
- Security Information and Event Management (SIEM):
- Implement a SIEM solution to collect, analyze, and correlate security logs from various sources, including firewalls, intrusion detection systems, and cloud service providers.
- SIEM systems can help detect and respond to threats in real-time, such as suspicious activity, malware infections, and data breaches.
- Cloud Security Posture Management (CSPM):
- Utilize CSPM tools to continuously assess and monitor your cloud environment for security misconfigurations and vulnerabilities.
- CSPM solutions can identify and remediate issues like insecure access controls, missing patches, and non-compliant resources.
- Regular Security Audits and Penetration Testing:
- Conduct regular security audits and penetration testing to identify and address1 any vulnerabilities in your security controls.
- This can help uncover weaknesses that might otherwise go unnoticed.
- Continuous Monitoring of Security Logs and Alerts:
- Continuously monitor security logs and alerts for any suspicious activity.
- Investigate and respond promptly to any security incidents.
- Regularly Reviewing and Updating Security Policies:
- Regularly review and update your security policies to reflect changes in your business environment, technology landscape, and the threat landscape.
- Ensure that your security controls are aligned with your evolving security needs.
By implementing these continuous monitoring and improvement practices, organizations can proactively identify and address security threats, maintain a strong security posture, and ensure the ongoing effectiveness of their Zero Trust security framework.
In the next section, we will discuss the benefits of implementing Zero Trust in cloud environments.
Benefits of Implementing Zero Trust
Implementing a Zero Trust security model offers numerous benefits for organizations:
- Enhanced Security Posture:
- By shifting the focus from perimeter security to identity and context, Zero Trust significantly enhances the overall security posture of an organization.
- It reduces the attack surface and makes it more difficult for attackers to gain unauthorized access to critical systems and data.
- Reduced Risk of Data Breaches and Cyberattacks:
- By implementing strong authentication, authorization, and data protection measures, Zero Trust minimizes the risk of data breaches, ransomware attacks, and other cyber threats.
- Improved Compliance with Industry Regulations:
- Zero Trust principles align with many industry regulations, such as GDPR, HIPAA, and PCI DSS.
- By implementing Zero Trust, organizations can demonstrate compliance with these regulations and avoid costly fines and penalties.
- Increased Business Agility and Operational Efficiency:
- Zero Trust can improve business agility by enabling secure and flexible access to resources from anywhere.
- It can also improve operational efficiency by streamlining access control processes and reducing the administrative burden associated with managing security.
By embracing a Zero Trust security model, organizations can proactively address the evolving threat landscape, protect their critical assets, and gain a competitive advantage in today's digital world.