Laying the Groundwork: Risk Assessment & Management in Cybersecurity
When you hear "cybersecurity", what's the first thing that comes to mind? For many, it's a mental image of complex software, impenetrable firewalls, or perhaps a stern-faced IT expert staring at glowing screens. But here's a secret: cybersecurity is far more than just buying the latest tech solutions. It's about a proactive mindset, a continuous process of understanding, anticipating, and responding to the digital threats that loom over our connected world. It's about looking beyond the buzzwords and grasping the fundamental principles that truly safeguard your digital life and business.
At its heart, cybersecurity is about asking the crucial "what if?" questions: What if a hacker gains access to our customer data? What if our website goes down? What if a phishing email tricks an employee? And, critically, how bad would that really be? These "what if" scenarios, and the potential harm they represent, are what we call risk.
That's where Risk Assessment and Management come in. These aren't just fancy corporate terms; they're the foundational steps—the very groundwork—for truly protecting your digital assets. Risk assessment is like peering into a crystal ball to identify potential dangers, while risk management is about having a solid plan to either avoid those dangers or minimize their impact. Together, they form the backbone of any effective cybersecurity strategy.
Understanding Cybersecurity Risk: The Core Components
To effectively manage cybersecurity, you first need to understand what "risk" truly means in this context. It’s not just a vague feeling of danger; it’s a measurable concept built from specific ingredients.
Risk Defined: A simple explanation:
At its most basic, Risk can be understood as the potential for loss or harm when a threat exploits a vulnerability, leading to a negative impact. Think of it like a simple equation:
Risk = Threat × Vulnerability × Impact
Let's break down each component of this equation.
I. Threats: The "Who" or "What" Wants to Do Harm:
Definition: A threat is any potential cause of an unwanted incident that might harm an organization or individual. It's the "actor" or "event" that has the potential to exploit a weakness and cause damage.
Examples:
- Malicious Actors: Hackers, cybercriminals, state-sponsored groups, disgruntled employees (insider threats).
- Malware: Viruses, ransomware, spyware, Trojans that can infect systems.
- Phishing/Social Engineering: Deceptive tactics used to trick individuals into revealing sensitive information or performing actions that compromise security.
- Natural Disasters: Earthquakes, floods, fires that can physically damage data centers or equipment.
- System Failures: Hardware malfunctions, software bugs, power outages.
- Human Error: Accidental deletion of data, misconfigurations, falling for phishing scams.
II. Vulnerabilities: The "Weaknesses" They Exploit:
Definition: A vulnerability is a flaw, weakness, or loophole in a system, process, or configuration that a threat can exploit to cause harm. It's the "door" that a threat might use to get in.
Examples:
- Unpatched Software: Operating systems, applications, or firmware that haven't received the latest security updates, leaving known holes open.
- Weak Passwords: Easily guessable passwords, default credentials, or reused passwords that are susceptible to brute-force attacks.
- Misconfigured Firewalls/Systems: Security settings that are too lenient, allowing unauthorized access or traffic.
- Lack of Employee Training: Employees unaware of phishing tactics or secure computing practices, making them susceptible to social engineering.
- Open Network Ports: Unnecessary services running or ports left open on a network, providing entry points for attackers.
- Outdated Hardware: Devices that no longer receive security support or patches.
III. Impact: The "Damage" If It Happens:
Definition: Impact refers to the consequences or adverse effects that result if a security incident occurs and a threat successfully exploits a vulnerability. It's the "cost" of the risk materializing.
Examples:
- Financial Loss: Direct monetary theft, ransom payments, costs of recovery, lost revenue due to downtime.
- Data Breach: Exposure, theft, or loss of sensitive customer data, intellectual property, or personal information.
- Reputational Damage: Loss of customer trust, negative public perception, damage to brand image.
- Operational Disruption: Downtime of critical systems, interruption of business processes, inability to deliver services.
- Legal and Regulatory Penalties: Fines for non-compliance with data protection laws (e.g., GDPR, HIPAA), legal fees from lawsuits.
- Loss of Intellectual Property: Theft of trade secrets, proprietary algorithms, or product designs.
By understanding these three core components – Threats, Vulnerabilities, and Impact – you can begin to systematically analyze the cybersecurity risks facing your digital assets, setting the stage for effective management.
Step 1: Cybersecurity Risk Assessment – Finding the Dangers
Now that we understand what makes up a risk, the next logical step is to actively go out and find them. This is where Cybersecurity Risk Assessment comes into play.
What is Risk Assessment?
Risk assessment is the systematic process of identifying, analyzing, and evaluating the potential risks to your digital assets. It's like a security detective's investigation, where you meticulously look for potential problems before they become actual disasters. The goal is to gain a clear picture of what could go wrong, how likely it is, and what the consequences would be.
Key Stages of a Basic Risk Assessment:
Even without complex tools, you can perform a foundational risk assessment by following these key stages:
- Identify Assets:
The very first step is to know what you're trying to protect. This isn't just about physical hardware; it's about anything of value in your digital world.
What needs protecting? Think broadly:
- Sensitive Data: Customer lists, financial records, employee data, intellectual property, trade secrets.
- Critical Systems/Applications: Your website, e-commerce platform, internal business applications, email servers.
- Hardware: Laptops, servers, networking equipment.
- User Accounts: Admin accounts, employee login credentials.
- Reputation: Your brand's standing in the market.
Why is it valuable? Understanding the inherent value (financial, operational, reputational) of each asset helps in prioritizing its protection.
- Identify Threats:
Once you know what's valuable, consider who or what might try to harm it. Brainstorm common threats relevant to your assets.
- Who might attack these assets? (e.g., individual hackers, organized cybercrime groups, disgruntled employees, competitors).
- What kind of attacks? (e.g., ransomware, phishing, data breaches, denial-of-service (DoS) attacks, malware infections, physical theft, natural disasters like floods or power outages).
- Identify Vulnerabilities:
Now, think about the weaknesses that these threats could exploit to compromise your identified assets.
Where are the weaknesses that threats could exploit?
- Technical Flaws: Unpatched software, outdated operating systems, weak network configurations, open ports.
- Human Weaknesses: Lack of employee training, poor password hygiene, susceptibility to social engineering.
- Process Gaps: No clear data backup strategy, insufficient physical security for servers, lack of access control policies.
- Physical Weaknesses: Unsecured server rooms, easily accessible physical devices.
- Analyze Likelihood:
For each identified risk (Threat + Vulnerability impacting an Asset), consider how likely it is to actually occur.
- How likely is it that a specific threat will exploit a specific vulnerability?
- Categorize simply: Low, Medium, or High. (e.g., A brand-new, critical software vulnerability is High likelihood if unpatched; an asteroid hitting your server room is Low likelihood).
- Analyze Impact:
If the risk does materialize, what would be the consequences? Quantify the damage as best you can.
- If the risk materializes, what would be the financial, operational, and reputational consequences?
- Categorize simply: Low, Medium, or High. (e.g., Minor website glitch = Low impact; Complete data breach with regulatory fines = High impact).
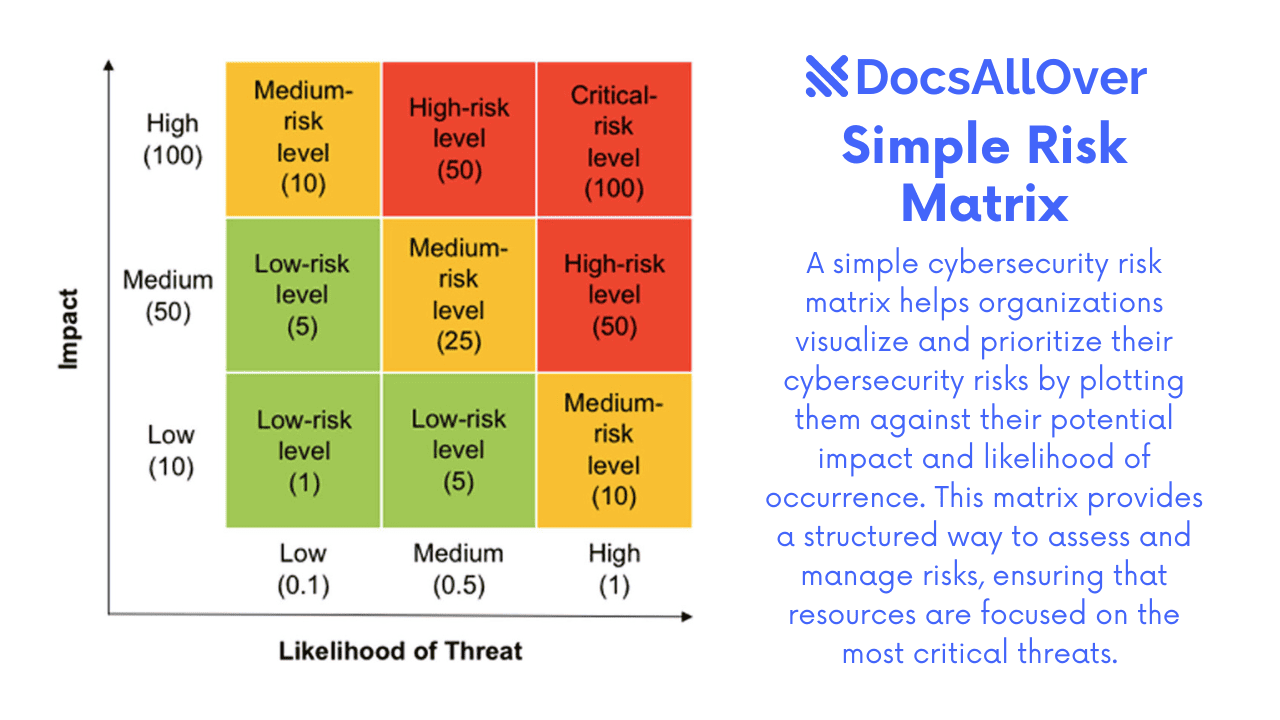
- Calculate Risk Level:
Combine your likelihood and impact assessments to determine an overall risk level. This helps you prioritize.
A simple Risk Matrix can be incredibly useful here. Multiply (or combine qualitatively) the Likelihood and Impact scores.
Step 2: Cybersecurity Risk Management – Taking Action
Once you've diligently assessed and identified your cybersecurity risks, the next crucial phase is to actively manage them. Cybersecurity Risk Management is about deciding what to do with the risks you've found and then putting those decisions into practice. It's the action phase, where you move from identifying potential problems to implementing solutions.
What is Risk Management?
Risk management is the ongoing process of deciding how to respond to your identified risks, implementing those responses, and then continuously monitoring and reviewing their effectiveness. It’s about being proactive rather than simply reacting when a security incident occurs.
Four Common Risk Response Strategies (The "What to Do About It"):
When faced with an identified risk, you generally have four fundamental strategies to choose from:
- Avoid:
- This strategy involves eliminating the activity or system that is causing the risk altogether. It's the most effective way to deal with a risk, as you remove the threat entirely.
- Example: Deciding not to store highly sensitive customer data on a publicly accessible server because the risk of a breach is too high and unacceptable. If you don't need the data, don't keep it.
- Mitigate (Reduce):
This is the most common and often the most practical strategy. It involves implementing controls to lower either the likelihood of the risk occurring or the impact if it does.
Examples:
- Patching: Regularly updating software and systems to fix known vulnerabilities (reduces likelihood).
- Multi-Factor Authentication (MFA): Requiring more than just a password for login (reduces likelihood of unauthorized access).
- Employee Training: Educating staff about phishing, secure Browse, and data handling (reduces likelihood of human error).
- Encryption: Scrambling sensitive data so it's unreadable if stolen (reduces impact).
- Regular Backups: Creating copies of critical data so it can be restored after an incident (reduces impact).
- Firewalls and Intrusion Detection Systems (IDS): Blocking malicious traffic and detecting suspicious activity (reduces likelihood).
- Strong Password Policies: Enforcing complex and unique passwords (reduces likelihood).
- Transfer:
- This strategy involves shifting the financial or operational responsibility of a risk to a third party. You're not eliminating the risk, but you're not solely bearing its consequences.
- Example: Purchasing cybersecurity insurance. If a data breach occurs, the insurance policy helps cover the financial losses, legal fees, and recovery costs, transferring a portion of the financial impact. Another example could be outsourcing a highly sensitive system to a specialized security vendor who then takes on certain operational risks.
- Accept:
- This strategy involves acknowledging the risk and its potential impact, and consciously deciding not to take any further action to avoid, mitigate, or transfer it. This is typically done for risks that have a very low likelihood and/or a very low potential impact, where the cost of managing them outweighs the potential benefit.
- Example: Acknowledging the very low risk of a specific minor website glitch that might occur once a year and only affects a handful of users, deciding that the cost of fixing it permanently is not justified. This decision should always be a conscious, documented choice, not simply an oversight.
Implementing Controls: Turning Strategies into Action
Once you've chosen your risk response strategy (most commonly mitigation), the next step is to actually implement the security controls. This means putting the chosen technical solutions (like installing firewalls, enabling MFA) and procedural changes (like new employee training programs, backup schedules) into practice. It's where your theoretical plan becomes tangible.
Monitoring and Review: Risk management is an ongoing cycle, not a one-time event
Cybersecurity threats and vulnerabilities are constantly evolving. Therefore, risk management is not a task you complete and forget about. It's a continuous, cyclical process:
- Monitor: Regularly check if your implemented controls are working effectively. Are there new threats emerging? Are previous vulnerabilities still present?
- Review: Periodically re-assess your risks. Have new assets been added? Have business operations changed? Are the likelihood and impact assessments still valid?
- Adapt: Adjust your strategies and controls as needed based on new information from monitoring and review.
This continuous cycle ensures that your cybersecurity defenses remain relevant and effective against the ever-changing landscape of digital threats.
Getting Started with Risk Assessment & Management (Practical Tips for Beginners)
Diving into cybersecurity risk assessment and management might seem daunting, especially if you're new to the concept. But you don't need to be a cybersecurity expert or have a massive budget to start laying this crucial groundwork. Here are some practical, beginner-friendly tips to help you get started:
Start Small:
Don't try to assess your entire digital ecosystem all at once. That can lead to analysis paralysis. Instead, focus on your most critical assets first. What data or systems are absolutely essential for your business or personal life? What would cause the most harm if compromised? Begin with those high-value targets, learn the process, and then gradually expand your scope. For instance, if you run a small online store, start with your customer database and payment processing system before moving to less critical internal tools.
Use Simple Tools:
You don't need expensive, complex GRC (Governance, Risk, and Compliance) software to begin. For initial assessments, simple tools like spreadsheets (Google Sheets, Microsoft Excel) or basic templates are perfectly adequate.
- Create columns for "Asset," "Threat," "Vulnerability," "Likelihood (Low/Med/High)," "Impact (Low/Med/High)," "Risk Level," "Mitigation Strategy," and "Responsible Party."
- This helps you organize your thoughts and capture the essential information without an overwhelming learning curve for new software.
Involve Your Team:
Cybersecurity isn't just an IT department's responsibility; it's everyone's. Everyone has a role to play in identifying risks from their unique perspective.
- Employees on the front lines might spot phishing attempts more quickly.
- Sales or marketing might know which data is most valuable to competitors.
- Encourage an open culture where potential weaknesses or concerns are shared, not hidden. A simple brainstorming session can uncover surprising insights.
Prioritize:
Once you've identified a handful of risks, you'll likely realize you can't tackle everything at once. This is where the risk matrix comes in handy. Focus on the highest-risk items first – those with high likelihood and high impact. Addressing these critical vulnerabilities will give you the most significant immediate security uplift for your efforts. Don't get bogged down trying to fix every "Low Risk" item when a "Critical Risk" is staring you down.
Document Everything:
This step is often overlooked but is incredibly important. Keep clear, concise records of identified risks, your assessment of them, and your management decisions.
- Document what the risk is, why you assigned a certain likelihood and impact, what strategy you chose (avoid, mitigate, transfer, accept), what controls you implemented, and who is responsible for maintaining those controls.
- Good documentation helps you track progress, ensures consistency, and provides a valuable reference for future reviews. It's also crucial if you ever need to demonstrate due diligence for compliance purposes.
Don't Be Afraid to Ask for Help:
While you can certainly start this journey on your own, there will come a point where specialized expertise is beneficial. Don't hesitate to consider external experts when:
- You deal with highly sensitive data (e.g., financial, medical, personal customer information).
- Your systems become too complex for your internal team to manage.
- You need specialized assessments like penetration testing or vulnerability scanning.
- You're struggling with specific compliance requirements. A reputable cybersecurity consultant can provide invaluable guidance, perform deeper analyses, and help you mature your risk management program.
By understanding what threats lurk, recognizing your own vulnerabilities, and evaluating the potential impact of a breach, you move from a reactive stance to a proactive one. You're no longer simply waiting for something bad to happen; instead, you're identifying, prioritizing, and strategically addressing risks before they escalate. This shift empowers you to build a truly resilient digital foundation, one that can withstand attacks and quickly recover from incidents.
So, don't wait for a cybersecurity incident to force your hand. Take control of your digital security today. Start by taking those first, practical steps we outlined: identify your critical assets, brainstorm potential threats, look for weaknesses, and begin prioritizing your risks.